That appears to have worked in the lab Boris! Prod soon. Thank you.
izelt
@izelt
Posts made by izelt
-
RE: Penetration Testing Results - Some Issuesposted in general forum
-
RE: Penetration Testing Results - Some Issuesposted in general forum
Any update on this @bjrmatos ?
-
RE: Penetration Testing Results - Some Issuesposted in general forum
Hi Boris,
I can downgrade back to 2.2.0 and the server runs fine. Any time I go to 2.4.0 or greater, this red screen is presented. I've tried every version between 2.6.1 and 2.3.0, and they all show the red screen.
Yes, we're using fs.
I have included our config file in the zip (and also the start-up script, as it installs some specific npm modules into the docker container) - where should I email it to?
-
RE: Penetration Testing Results - Some Issuesposted in general forum
When upgrading from version 2.2.0 to 2.4.0 (or later) we get the following red wall of text. What's going wrong here?
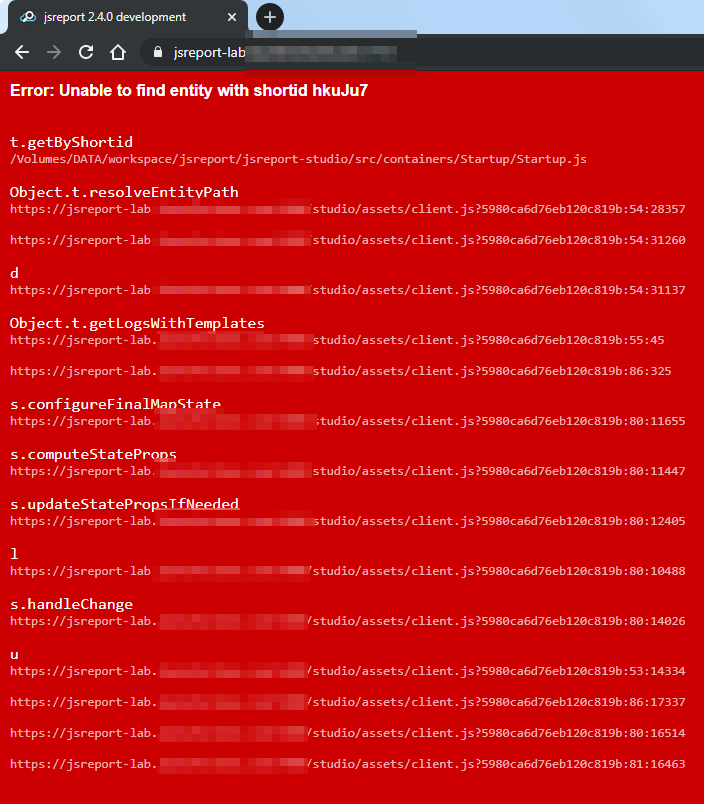
-
RE: Penetration Testing Results - Some Issuesposted in general forum
Thanks for the feedback Boris!
-
RE: Penetration Testing Results - Some Issuesposted in general forum
Much appreciated Jan - I'll wait for a follow up!
-
Penetration Testing Results - Some Issuesposted in general forum
We recently had a pen test conducted against our application, and its ancillary components, and there were three moderate issues raised specifically for the jsreport server (v2.2.0). Please provide any input you can to help us mitigate these:
Finding 1: Strict Transport Security Misconfiguration: There was no Strict-Transport-Security header in the server response. The HTTP Strict Transport Security policy defines a timeframe where a browser must connect to the web server via HTTPS.
Is this configurable via the jsreport conf, or docker host?
Finding 2: Auto-completed Password Fields: The password auto-complete feature allows users to have the browser automatically fill the password field with previously submitted values when a user begins entering the password. Unless specifically disabled, this feature is enabled by default.
Can you confirm this was fixed in 2.4.0? If so, we will renew our subscription and update to the latest version
Finding 3: DOM-Based Link Manipulation: DOM-based vulnerabilities arise when a client-side script reads data from a controllable part of the DOM (for example, the URL) and processes this data in an unsafe way. DOM-based link manipulation arises when a script writes controllable data to a navigation target within the current page, such as a clickable link or the submission URL of a form.
Problem line of code below is: form.action = window.location.pathname + window.location.search;
var form = document.getElementById("loginForm"); if (window.location.pathname.lastIndexOf("login", 0) === 0) { form.action = window.location.pathname + window.location.search; } else { if (window.location.search.indexOf("returnUrl") === -1) { form.action = "/login?returnUrl=" + encodeURIComponent(window.location.pathname + window.location.hash + window.location.search); } else { form.action = "/login" + window.location.search; <SNIP>This looks to be squarely in your code, and I can't see any mention of a fix in the release notes for versions after v2.2.0. Can you please comment?
-
Docker in Dev Modeposted in general forum
How do we run a docker instance of jsreport in dev mode? It always reads in the prod.config.json
-
RE: User Creation & Managementposted in general forum
Already had the admin account set.
Your screenshot helped though! The User section was hidden because of the frame edge. I didn't notice the scrollbar to show there were more sections available:
 .
.