I'm really just looking for help preventing this alert to satisfy my security team. Is there anyway to prevent the binary process from being killed automatically? I apologize as I'm really not familiar with anything behind the scenes. I'm just looking for a remedy so I don't need to find another PDF solution when this one works great because of these alerts.
atrichardson
@atrichardson
Posts made by atrichardson
-
RE: JSReport webshell causing CrowdStrike alertsposted in .net sdk forum
-
RE: JSReport webshell causing CrowdStrike alertsposted in .net sdk forum
Apparently this is still throwing alerts for some reason. Should simply removing .KillRunningJsReportProcesses() take care of this? Or is there something more I need to do to prevent this from happening?
-
RE: JSReport webshell causing CrowdStrike alertsposted in .net sdk forum
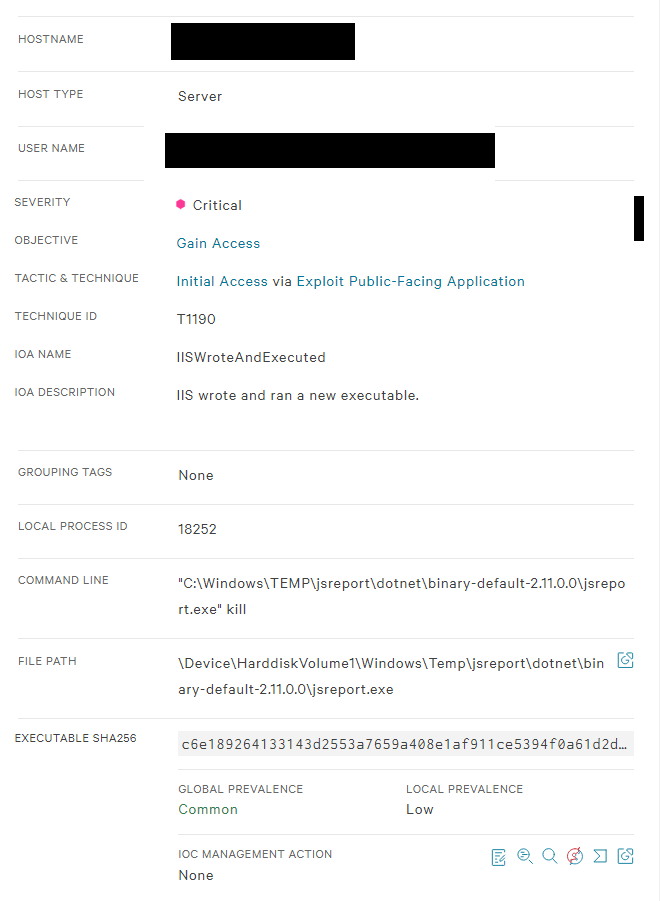
Sorry, I must have misunderstood what was happening. It doesnt appear to be JSReport itself thats causing problems. It appears to be IIS downloading and executing over and over that's being flagged. Is there any way to store the executable on the server and reference that instead of downloading and running the exe?
-
JSReport webshell causing CrowdStrike alertsposted in .net sdk forum
I'm using JSReport for HTML to PDF and my InfoSec team is getting alerts due to the download and running of JSReport, is there anything I should be doing that would prevent this?
In my Startup.cs I've started the service as follows:
services.AddJsReport(new LocalReporting().UseBinary(JsReportBinary.GetBinary()).KillRunningJsReportProcesses().AsUtility().Create());In my controller I'm using the ChromePdf recipe
HttpContext.JsReportFeature().Recipe(Recipe.ChromePdf)