JSReport Puppeteer vulnerabilities
-
Hello JSReport Support Team,
During our latest AWS Inspector security scan on the JSReport production deployment, multiple critical and high-level vulnerabilities were detected originating from the Puppeteer dependency bundled with JSReport.
We request guidance on the following:
• Whether there is a patched/updated JSReport release that resolves the Puppeteer-related vulnerabilities.
• If there is a recommended workaround or manual upgrade process for Puppeteer versions inside JSReport.
• Any official security best practices to mitigate this issue while continuing to run JSReport in production?This vulnerability is impacting our production security compliance, so we request your assistance as soon as possible.
Thanks and Regards,
Gaurav Kelkar
-
The dependencies will be updated with the next release as always.
https://github.com/jsreport/jsreport?tab=readme-ov-file#vulnerabilitiesThe release is scheduled for this week.
-
Hello,
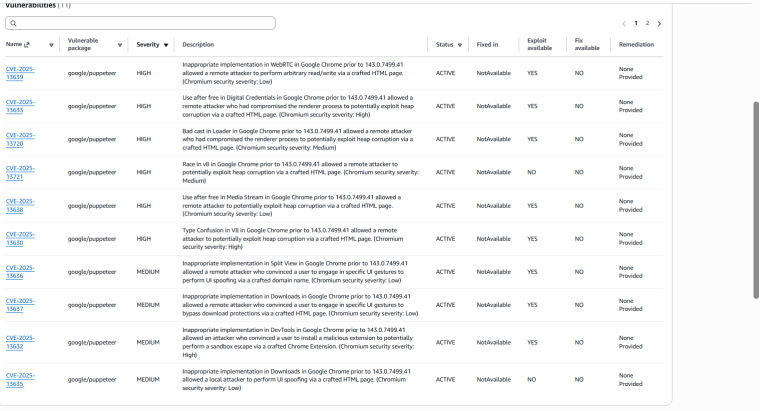
There are still some puppeteer related vulnerbilities are present.
All are in high in state so it is possible to provide one more update for this?Regards
-
We will again update puppeteer/chromium in the next release. As always. Likely soon.
If you need to update just now, go ahead and update the puppeteer dependency.
You just need to list the latest puppeteer dependency in your package.json.Or build your own Docker image with the updated Chromium. However, note that the latest Chromium with the fix is not yet in the public repository at the time of writing this post.